Few things compare to the fear you feel when you suspect or (even worse) can confirm that your computer or phone has been hacked. Malware attacks are becoming more common and the feeling remains the same: a sense of being violated and a helplessness at not knowing what data that attacker is snatching and where it will end up. The best remedy is prevention — but, once you do experience a malware attack, it’s important to act fast. A malware attack can ultimately end with hackers taking complete control of your computer or phone and its data. Whether the culprit is a virus, ransomware, or a trojan horse, red flags to look for include your apps crashing more often, unusual website activity that you didn’t initiate, and a battery that dwindles down fast. This is the one browser setting you should turn on immediately in case of a malware attack — and a few important tips to help prevent it from happening again.
Turn On Clear History
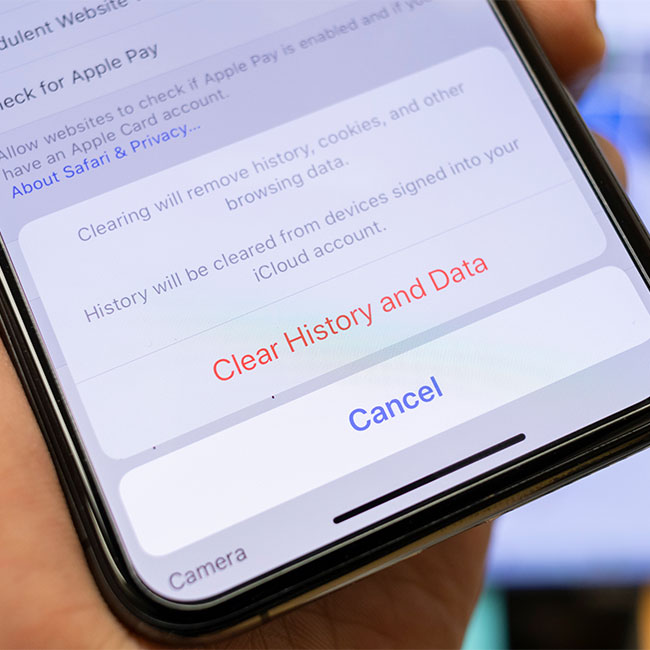
One of the major ways your device becomes infected with malware is via a link you unknowingly opened that was sent to you from a suspicious source. The first thing you should do is head over to your browser settings and tap Clear History and Website Data and then tap Clear History and Data. This simple step can help remove malware that was sent to you via a message and a link. In addition, make sure you delete any apps that you didn’t download yourself — these could also be the source of malware.
Shield Yourself From Future Malware Attacks
Now comes the single most important thing you can do: shield yourself from malware attacks. Take these three steps to protect yourself, according to Tech Expert Nely Mihaylova, a content executive at Scooter. guide.
Develop Your Email Skills
“Phishing campaigns are still active, but thieves have improved much since the days of the Nigerian prince begging for your cash,” Mihaylova says. “To view links’ correct URLs, hover over them. Additionally, verify that the email came from the person or business that claims to have sent it. If you’re unsure, pay attention to poor formatting and sentence construction. Do a quick Internet search for the topic line if something still appears off. There’s a chance that others have been conned and reported online.”

Install a Firewall
“If your OS didn't arrive with a firewall already installed, download one now,” Mihaylova says. “Other security tools to download include anti-malware software with different technologies to guard against spyware, ransomware, and exploits. (You should check to see if your OS has a firewall and an antivirus program and if those tools are compatible with other cybersecurity software.)”
Be Diligent With Personal Info Before Selling Your Device
“On any device, you intend to sell, remove all traces of your personal information,” Mihaylova says. “When erasing your hard disc, think about utilizing d-ban. This significantly increases the difficulty of retrieving information for anybody attempting to pillage your recycling devices. The platters on which the information is stored should be removed and destroyed if the information is important enough to be protected.”
And don’t forget the security basics: enable 2-factor authentication where you can and create different unique, complex passwords for each and every site you visit to better secure yourself from hackers.


























